in this article and in the incoming next articles i will cover all those topic , that will help you in writing a program , that is used in many designing eg in making calculator , logical operation etc , here its some describation of programming and a computer, or some mobile etc these programe are built in a device and come by default.
What is computer?
Computer
A device capable of performing computations and making logical decisions
A machine that manipulates data according to a list of instructions.
A programmable device that can store, retrieve, and process data.
Computer programs
Sets of instructions that control a computer’s processing of data
Hardware
Physical part of the computer
Various devices comprising a computer
Examples: keyboard, screen, mouse, disks, memory, CD-ROM, and processing units
Software
A collection of computer programs, procedures and documentation that perform some tasks on a computer system
Programs that run a computer
Computer organization
There are Six logical units in every computer:
Input unit
Obtains information (data and computer programs) from input devices (keyboard, mouse)
Output unit
Outputs information to output device (screen, printer) or to control other devices.
Memory unit
Rapid access, low capacity, stores input information
Arithmetic and logic unit (ALU)
Performs arithmetic calculations and logic decisions
Central processing unit (CPU)
Supervises and coordinates the other sections of the computer
Secondary storage unit
Cheap, long-term, high-capacity storage, stores inactive programs
Computer languages
Computer languages are divided into three types.
Machine languages
Machine language is machine dependent.
Strings of numbers giving machine specific instructions
Example:
+1300042774 +1400593419 +1200274027
Assembly languages
English-like abbreviations representing elementary computer operations (translated via assemblers)
Example:
LOAD BASEPAY ADD OVERPAY STORE GROSSPAY
Translator programs called assembler were developed to convert assembly language programs to machine language programs at computer speed.
High-level languages
Similar to everyday English, use mathematical notations (translated via compilers)
Example:
grossPay = basePay + overTimePay
C, C++ are the most widely used high level languages. Some other examples are
FORTRAN (formula translator)
Used in scientific and engineering applications
COBOL (common business oriented language)
Used to manipulate large amounts of data
Pascal
Used to teach structured programming
Translator programs called Compilers converts high-level language programs into machine language
Object technology
Models the real world with groups of interacting objects
Object technology is a packaging scheme that helps create Meaningful software units
Date objects, time objects, paycheck objects, invoice objects, audio objects, video objects, file objects, record objects, etc.
Any noun can be represented as an object
Reusable software components that model real world items
More understandable, better organized and easier to maintain than procedural programming
Favor modularity
Java and C++ are popular object oriented languages.
Allows development of more error free and reliable software.
Basics of C++ environment
Phases of C++ Programs
to be executed
1 EdiD
2 process
3 Compile
4 Link
5 Load
6 Execute
Program organization
Program statement
Definition
Declaration
Action
Executable unit
Named set of program statements
Different languages refer to executable units by different names
Subroutine: Fortran and Basic
Procedure: Pascal
Function : C++
C++ programming
C++ program
Collection of definitions, declarations and functions
Collection can span multiple files
Advantages
Structured into small understandable units
Complexity is reduced
Overall program size decreases
Pseudo code
Artificial, informal language used to develop algorithms
Similar to everyday English
Not executed on computers
Used to think out program before coding
Easy to convert into C++ program
Only executable statements
No need to declare variables
Algorithm
A sequence of precise instructions which leads to a solution
Program
An algorithm expressed in a language the computer can understand
program design
Programming is a creative process
Program Design Process
Problem Solving Phase
Result is an algorithm that solves the problem
Implementation Phase
Result is the algorithm translated into a programming language
Program solving phase
Be certain the task is completely specified
What is the input?
What information is in the output?
How is the output organized?
Develop the algorithm before implementation
Experience shows this saves time in getting your program to run.
Test the algorithm for correctness
Implementation phase
Translate the algorithm into a programming language
Easier as you gain experience with the language
Compile the source code
Locates errors in using the programming language
Run the program on sample data
Verify correctness of results
Results may require modification of the algorithm and program
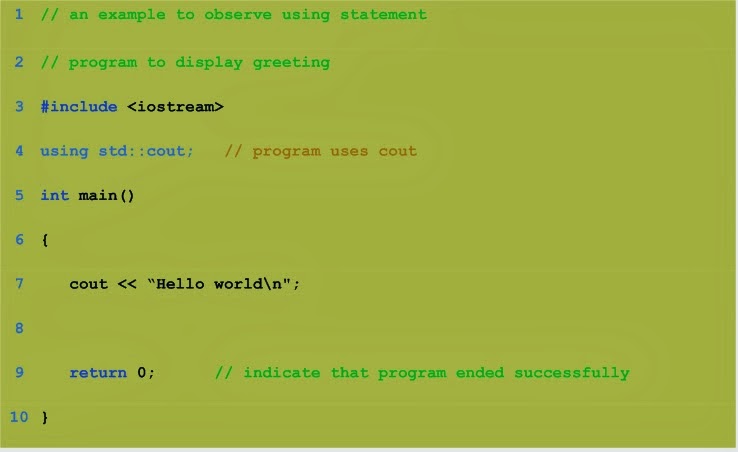
 |
| main program |
 |
| comments |
|
|
|
| the part will be discuss in the next article |
|
|
|
|
|